Implement a Real-Time Threat Intelligence & Defence Solution
Are your current cybersecurity tools built to stop attackers who use stolen credentials instead of malware?
Today’s cyber threats don’t always crash through your firewall. They slip in quietly, using valid credentials and behaving like trusted users. Identity-based threats are challenging to detect with traditional security systems. That’s why many organizations are turning to real-time threat intelligence and defence solutions to secure their business now and for the future.
In this post, you will learn what real-time threat intelligence is, why it’s a must-have in the modern threat landscape, and how to implement it effectively. You’ll also see how a reputable IT security partner, such as DNSnetworks, that can help you remain ahead.
Table of Contents:
- What is a Real-Time Threat Intelligence & Defence Solution?
- Key Challenges in Cybersecurity Without Real-Time Threat Defense
- Benefits of Implementing a Real-Time Threat Intelligence Solution
- Steps to Implement a Real-Time Threat Intelligence & Defence Solution
- How DNSnetworks Can Help
- Industry Trends and Future Outlook
What is a Real-Time Threat Intelligence & Defence Solution?
Real-time threat intelligence is the continuous collection, analysis, and response to cyber threat data as it happens. It combines data feeds, machine learning, behavioural analytics, and automated response mechanisms to detect and stop threats in their tracks.
This isn’t about reading yesterday’s threat reports. It’s about knowing, right now, if something suspicious is happening on your network.
Advanced technologies play a major role here:
- AI and machine learning uncover patterns that indicate malicious activity.
- Behavioural analytics track how users typically behave, flagging unusual actions.
- Cloud-based monitoring enables faster detection across hybrid environments.
Real-time threat intelligence is no longer optional. As identity-based threats become more common, the ability to spot irregular activity in real-time is essential to stop attackers before they cause damage.
Strengthen your security posture with our full-spectrum information security solutions that address risks across people, processes, and technology. Learn more.
Key Challenges in Cybersecurity Without Real-Time Threat Defense
Without real-time visibility into your network activity, you’re operating blind in a high-stakes environment.
Here are three major challenges businesses face:
- Increased Vulnerability to Zero-Day Attacks: Zero-day exploits often bypass signature-based detection. They’re unknown threats targeting undiscovered software flaws. Without a system that can analyse behaviour in real time, these threats go unnoticed until it’s too late.
- Delays in Identifying and Mitigating Threats : Manual investigation and remediation take time—time your attackers use to move laterally, escalate privileges, and extract data.
- Manual Processes Lead to Gaps: Traditional tools flood teams with alerts, many of which are false positives. Sifting through them manually wastes time and leads to real threats being overlooked.
Don’t wait for a breach to expose these gaps. Align your technology with your business goals through strategic IT consulting services from DNSnetworks’ seasoned experts. Learn more here.
Benefits of Implementing a Real-Time Threat Intelligence Solution
The right real-time threat intelligence platform offers more than detection; it gives your team the context, speed, and automation needed to shut down attacks fast.
1. Proactive Detection and Response
By analysing traffic and user behaviour as it happens, businesses can intercept attacks before they progress. This includes:
- Detecting suspicious login attempts using stolen credentials
- Blocking unauthorized privilege escalations
- Isolating endpoints showing signs of compromise
2. Minimized Downtime and Data Loss
With automated containment, you reduce the chance of business disruption. Systems can isolate affected assets and trigger incident response playbooks within seconds.
3. Enhanced Visibility into Threats and Vulnerabilities
Rather than drowning in raw alerts, teams get meaningful insights:
- Real-time threat mapping
- Risk scoring based on asset value
- Context around identity misuse, location anomalies, and more
Detect credential-based attacks early with identity threat detection and response tools built for today’s identity-first threat landscape. Learn more.
Steps to Implement a Real-Time Threat Intelligence & Defence Solution
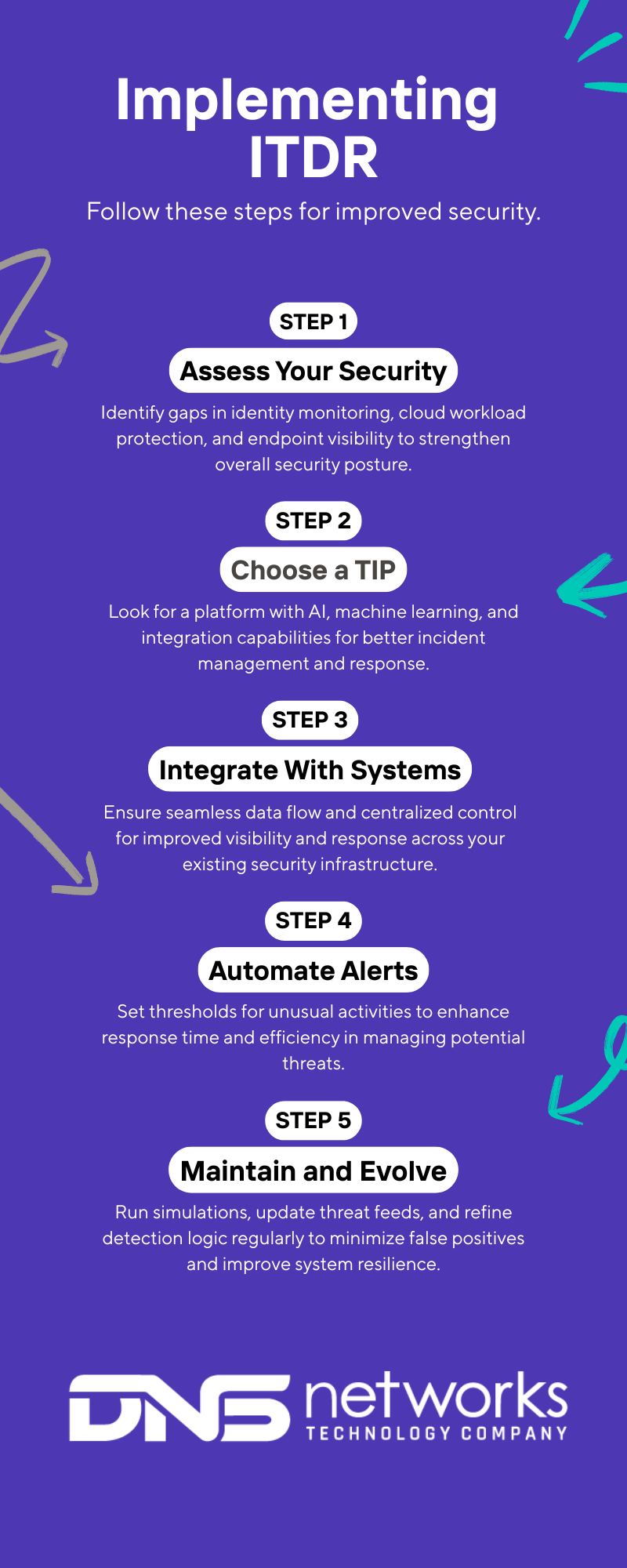
Rolling out real-time threat defence requires planning. Here’s a simplified roadmap:
Step 1: Assess Your Current Security Infrastructure
Identify gaps, especially around:
- Identity monitoring
- Cloud workload protection
- Endpoint visibility
Step 2: Choose a Threat Intelligence Platform (TIP)
Look for platforms with:
- Built-in AI and machine learning
- Integration with your SIEM, EDR, IAM systems
- Automated alerting and response
Step 3: Integrate With Your Existing Systems
Ensure smooth data flow across security tools. The goal is full visibility and central control.
Step 4: Automate Alerts and Incident Response
Set thresholds for unusual activity and predefine escalation paths. Automation is key to reducing response time.
Step 5: Maintain and Evolve
- Run red team simulations
- Update threat feeds regularly
- Refine detection logic based on false positive trends
Stay ahead of evolving threats with DNSnetworks’ advanced cybersecurity solutions powered by AI and real-time threat intelligence. Learn more .
How DNSnetworks Can Help
DNSnetworks delivers managed security services built around real-time threat intelligence and defence. Whether you’re an SME or a large enterprise, their tailored approach ensures your unique risks are addressed.
Expertise and Technology
- 24/7 security monitoring and incident response
- Deployment of AI-powered cybersecurity defence tools
- Identity Threat Detection and Response (ITDR) services
Custom Solutions
From financial institutions to healthcare providers, DNSnetworks offers scalable security solutions aligned with compliance requirements and threat profiles.
Proven Impact
Clients benefit from:
- Shorter detection and response times
- Greater visibility across endpoints and networks
- Stronger defences against credential-based attacks
See how DNSnetworks protects businesses like yours.
Get proactive IT support with our locally delivered Managed IT services in Toronto or Managed IT services in Montreal backed by local experts and 24/7 monitoring.
Industry Trends and Future Outlook
Cyberattacks are evolving rapidly. Here’s what forward-looking businesses should prepare for:
1. Growth of Identity-Based Threats
Attackers increasingly exploit stolen credentials to blend in. Real-time monitoring and ITDR will become foundational.
2. The Rise of Cloud-Based and Automated Platforms
Modern TIPs will offer:
- Cross-cloud integration
- Scalable machine learning pipelines
- Automated threat correlation
3. Intelligence-Led Security Strategies
Security operations will move toward:
- Threat-informed defence planning
- Prioritisation based on attacker behaviours
- Continuous threat modelling
Get in touch to get ahead of the curve with guidance from DNSnetworks.
Ready to Strengthen Your Cybersecurity Strategy?
Why wait for the next breach to figure out if your defences aren’t enough? Real-time visibility, faster response, and smarter defence are all within reach. Let’s modernize your cybersecurity game together. Get in touch today.

